Let's start with introduction of tools.
What is Kubescape?
Kubescape is Kubernetes (K8s) open-source tool which provides K8s cluster's configuration scanning, image scanning and Role-Based Access Control (RBAC) visualizer. Kubescape is developed by ARMO. It scans K8s clusters, YAML files, and Helm charts. It detects misconfigurations according to multiple frameworks (e.g. NSA, MITRE, etc.), and software vulnerabilities. It also showing RBAC violations.
It calculates risk scores for specific control and resource. It also shows overall risk score. Both risk score are in percentage (%). If risk score is low (0%), then it is great. If risk score is high (100%), then it is worst case and you should fix K8s cluster configuration based on Kubescape report. We can also create custom framework to scan K8s cluster based on our requirement.
It provides Command Line Interface (CLI). You can format output with different formats like JSON, PDF, etc. It can also integrates with other DevOps tools like Github Actions, Gitlab, etc.
It has UI (Armo management portal) which can accessible easily on our browser. So we can get more details for specific misconfiguration and fix it accordingly.
What is Github and its Actions?
Github is a platform for distributed version control using Git. It also provides more features like Github Actions, Github pages, etc.
Github Actions uses YAML file to define a workflow. It is in .github/workflows directory.
There are five components for Github Actions:
- Workflows: Configurable automated process and will run one or more jobs
- Events: Specific activity to trigger workflows
- Jobs: Set of steps in a workflow that execute on the same runner
- Actions: Custom application
- Runners: Server that run workflows when they are triggered
How to integrate Kubescape with Github Actions?
We will use Github platform to setup workflow for Kubescape.
- Go to Github and login into it. If you don't have account, then signup for it.
- Click on 'New' button to create a new repository
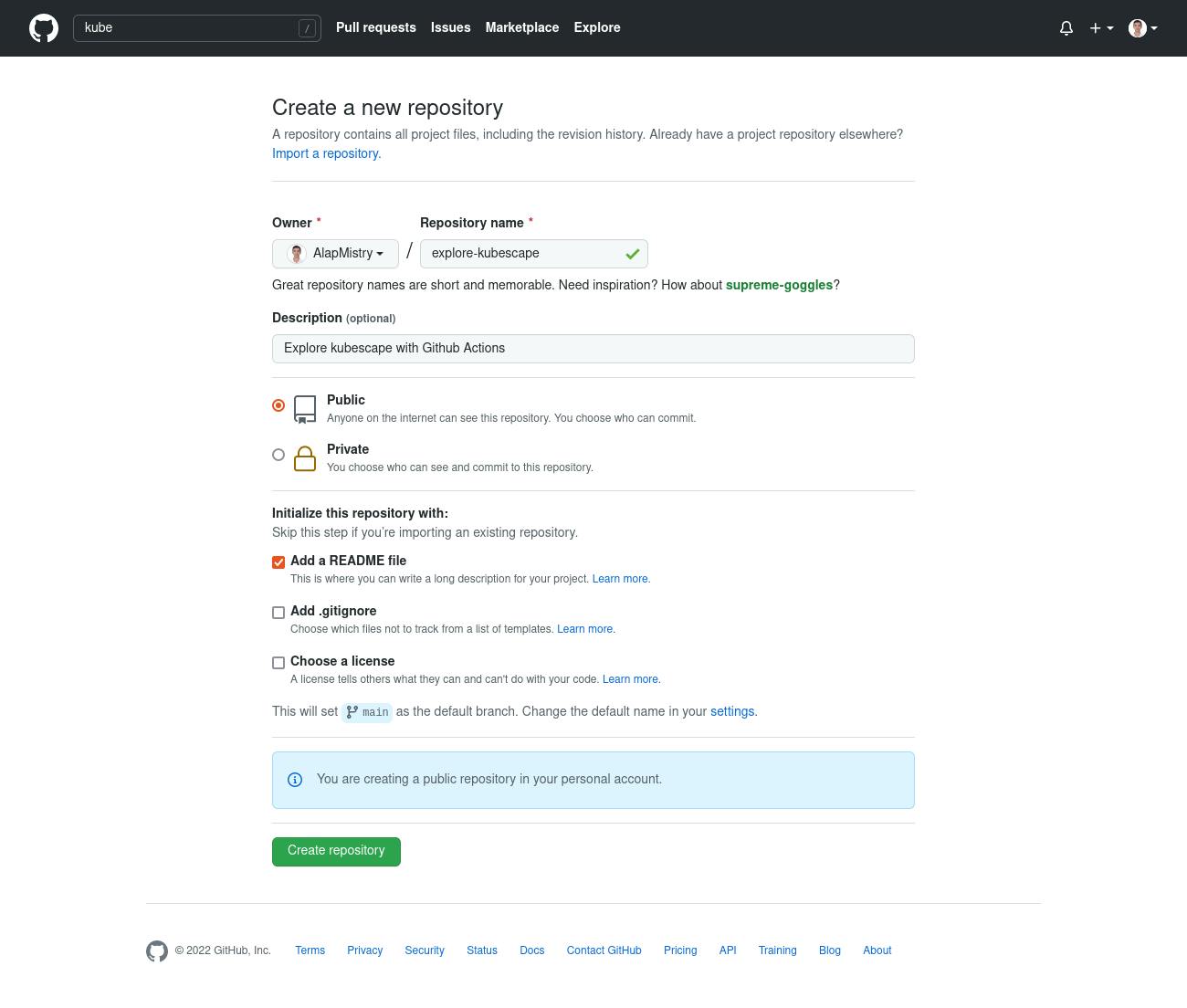
- Fill a new repository details
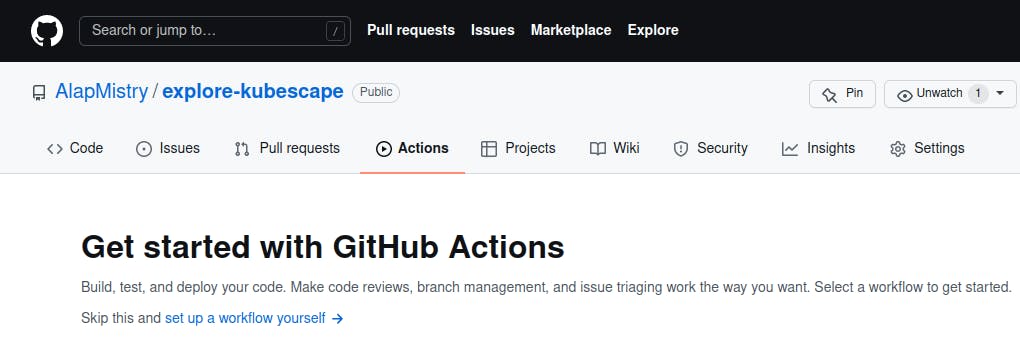
- Go to 'Actions' tab and click on 'set up a workflow yourself' link as we will implement a custom workflow
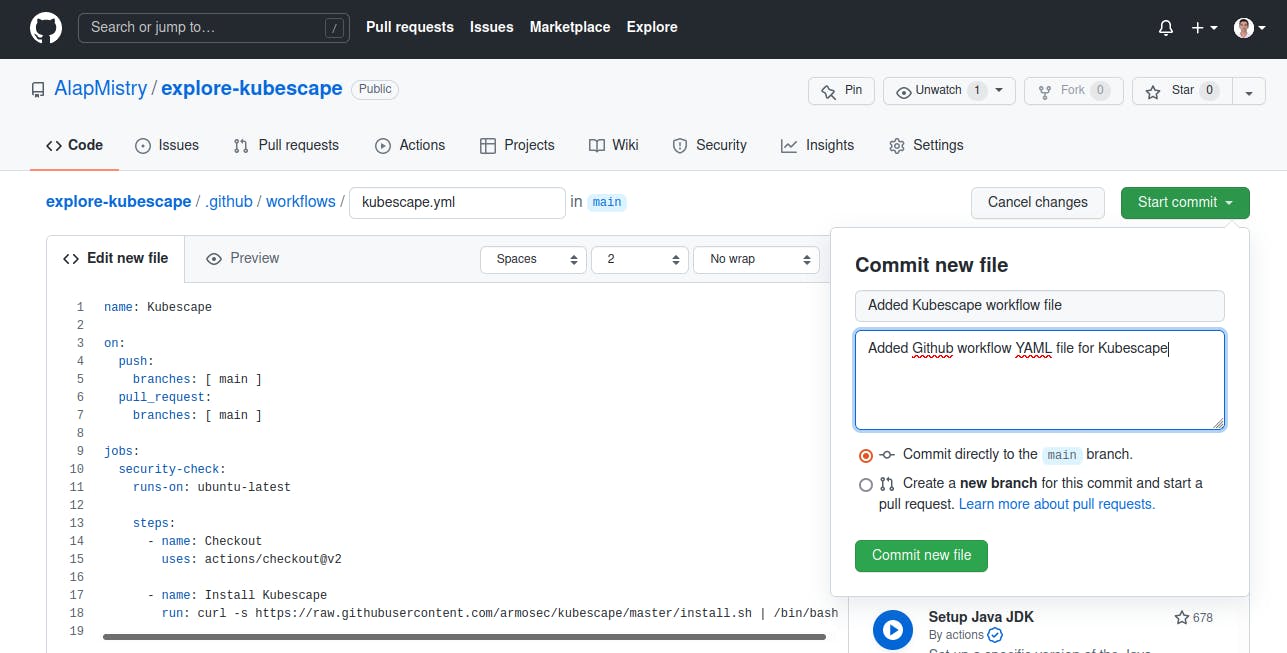
- Implement a workflow file, click on 'Start commit' button, fill commit message, and click on 'Commit new file' button. It will trigger workflow, but failed because we don't have any YAML file to scan. I am using 'main' branch for this example: (Don't worry. The complete file is on my Github)
- Click on 'Add file' dropdown and select 'Create new file' option
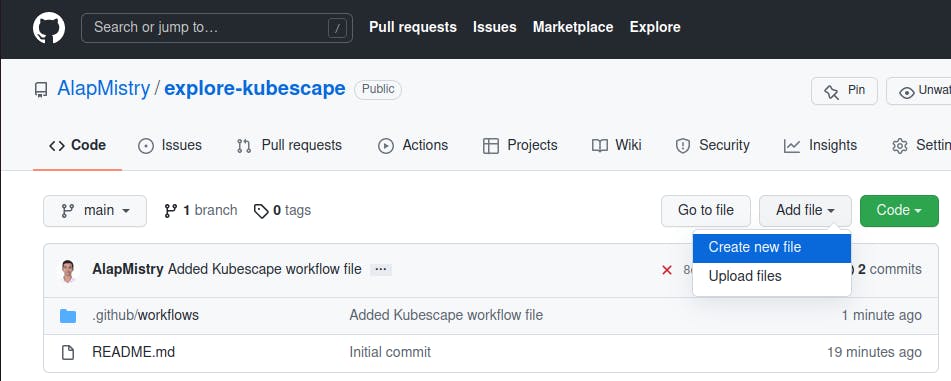
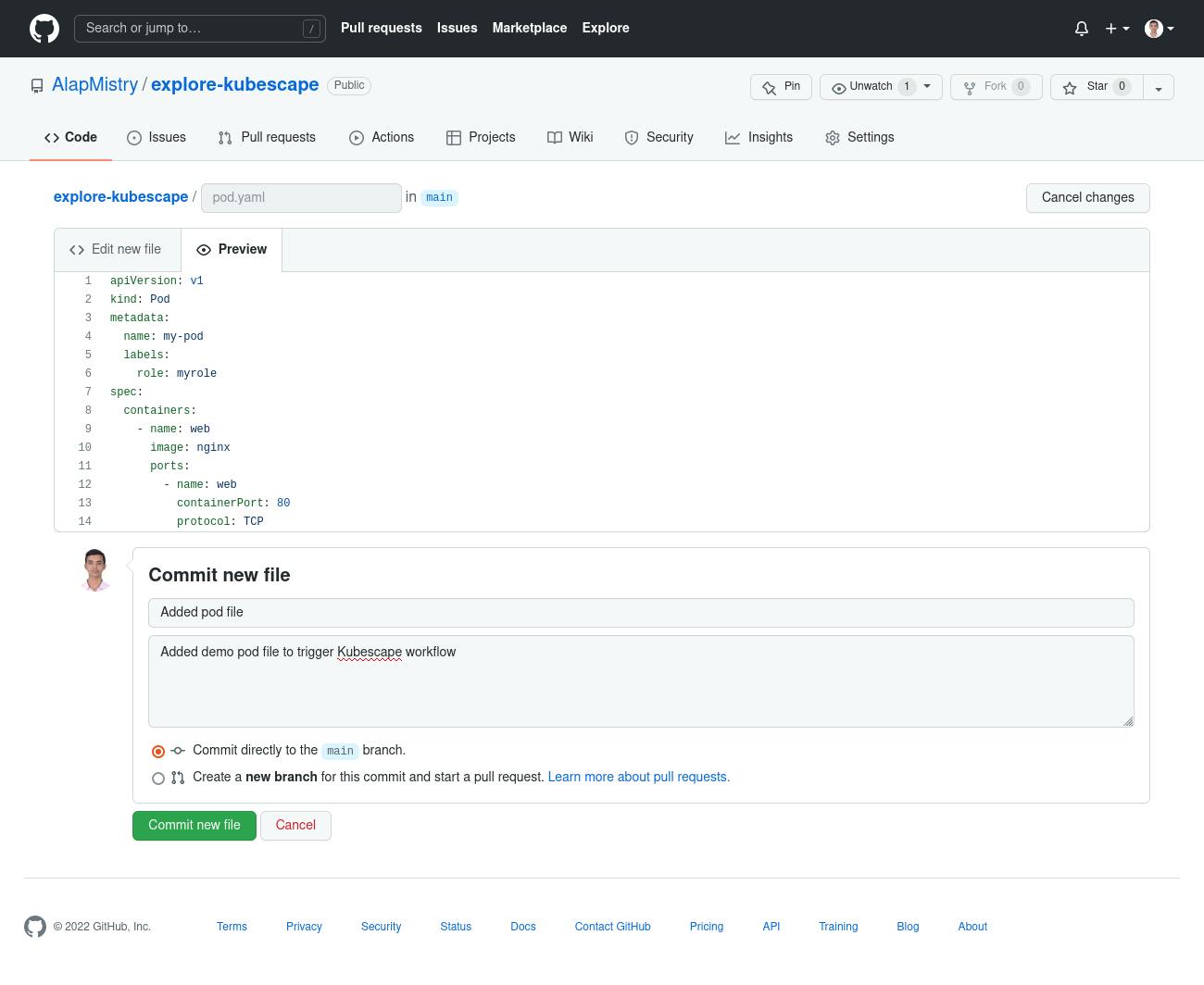
- Implement a pod file, click on 'Preview' tab, fill commit message, and click on 'Commit new file' button to trigger Kubescape workflow successfully
- Click on 'Actions' tab. You will see all workflows which are created.
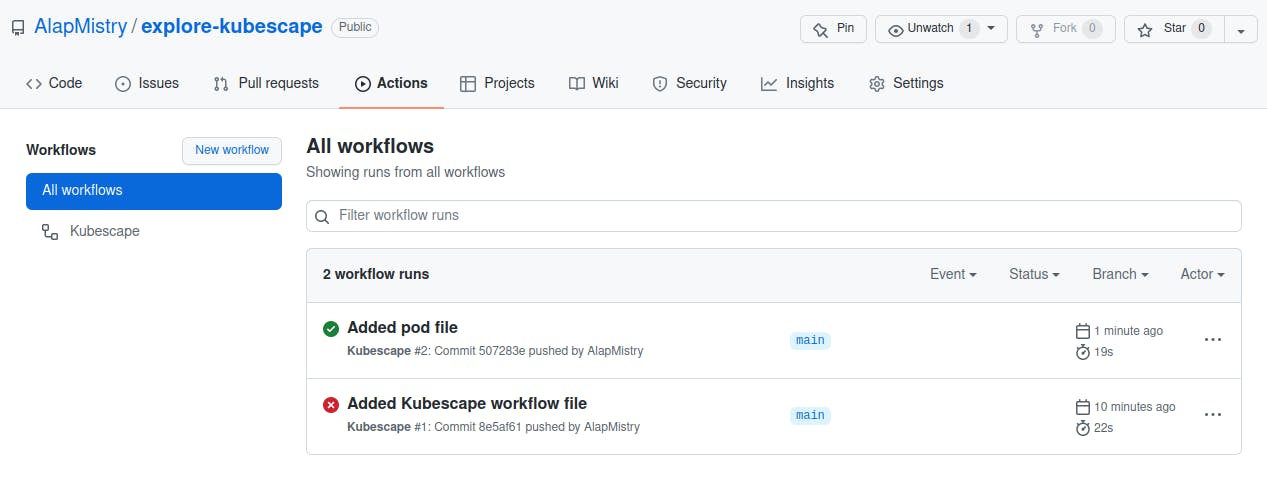
- There are two workflows executed. Click on last workflow (in my case 'Added Kubescape workflow file')
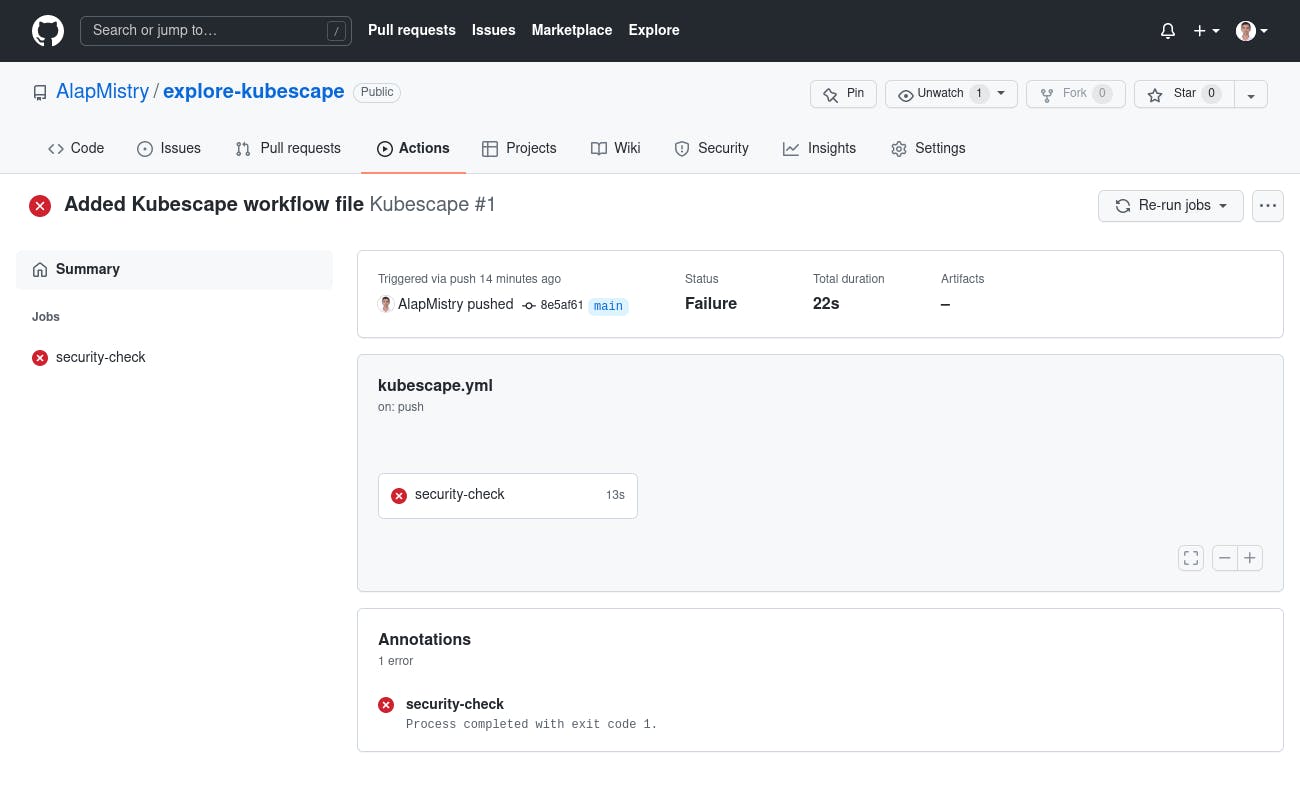
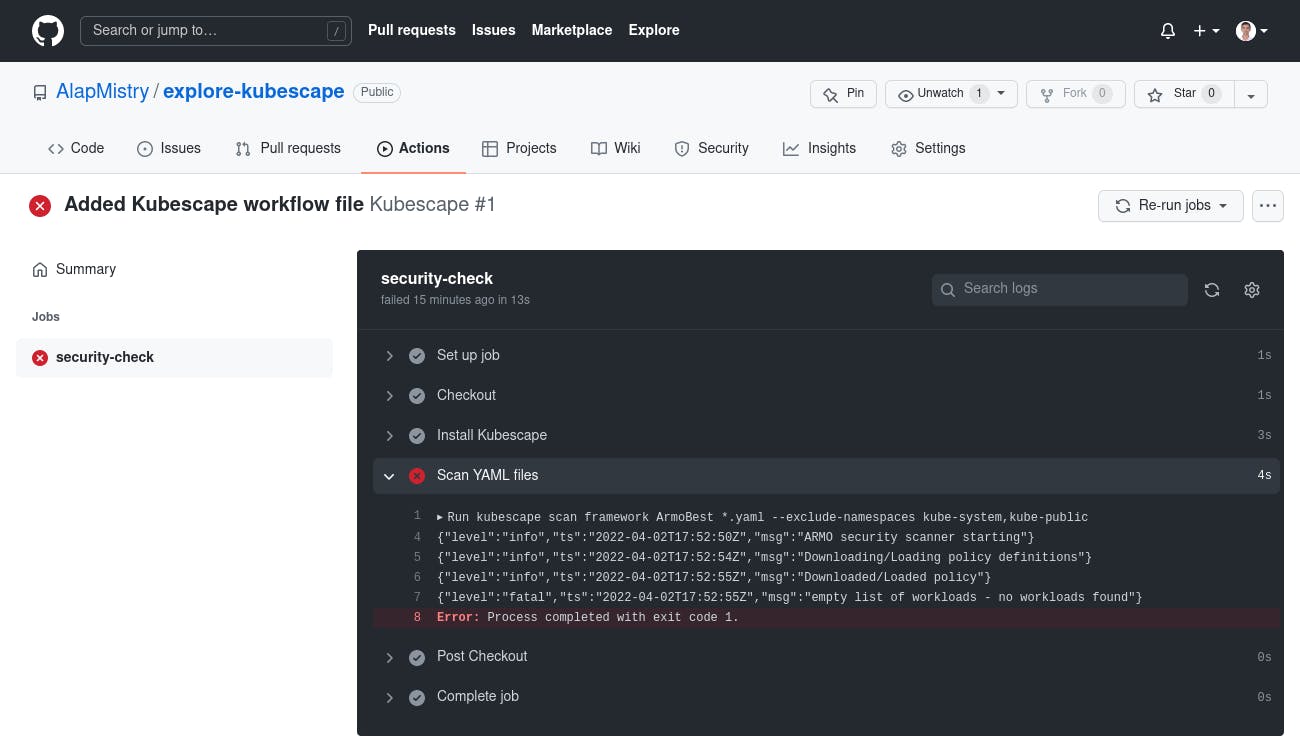
- Click on 'security-check' job and expand 'Scan YAML files' section. It shows fatal error with message because we hadn't any YAML file to scan at that time.
- Go back and click on first workflow (in my case 'Added pod file'). Click on 'security-check' job and expand 'Scan YAML files' section. Now, it shows Kubescape report in pretty printer format.
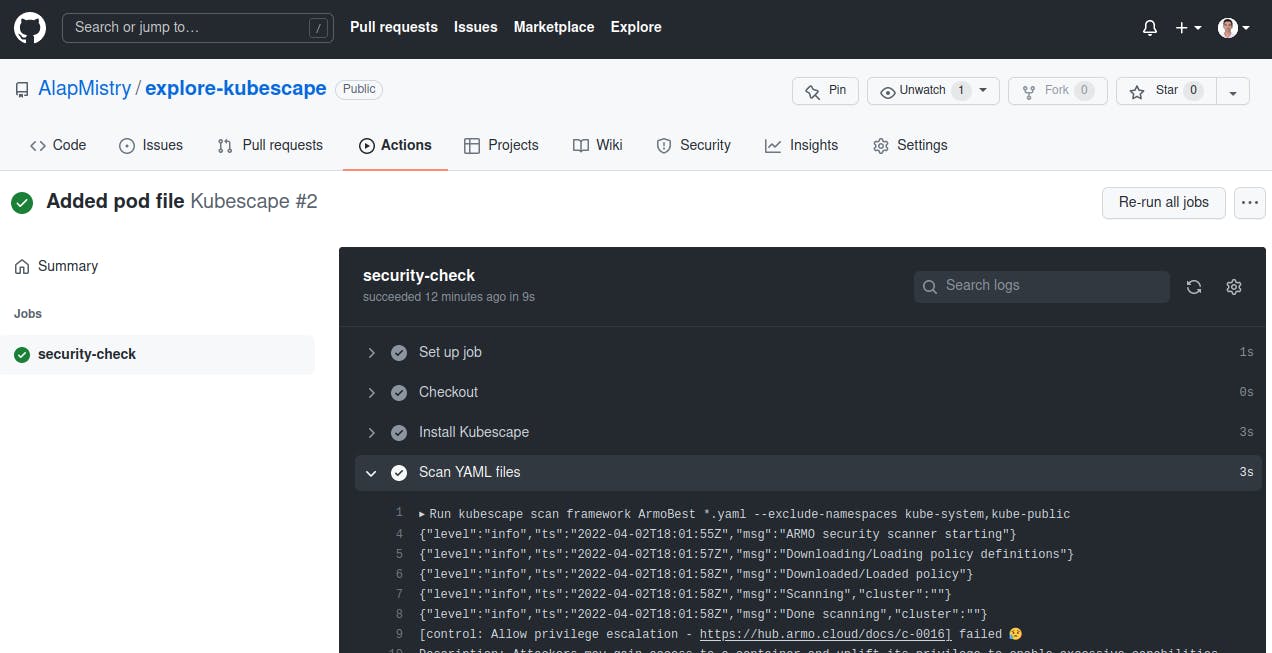
Congratulations! We successfully integrated Kubescape with Github Actions.
We can modify kubescape scan command based on our requirement. I like to use --submit option to get more details on Armo management portal. You can get more options from these Docs.
Which feature I requests to Kubescape team?
I requests Kubescape team to add feature which enables us to select sections, clusters and frameworks after logging into and before landing on the first page of Armo management portal.
